



Suggested citation: Dhruvak Aggarwal, Simran Kalra, Shalu Agrawal. 2023. Making India's Advanced Metering Infrastructure Resilient: Analysis of Power Systems from a Cyber Security Perspective. New Delhi: Council on Energy, Environment and Water.
Reaping the full benefits of smart meters for India’s power sector requires upstream devices that collect, transmit, store and analyse data in real-time, which comprises the Advanced Metering Infrastructure (AMI). As India proceeds with its ambitious rollout plan for consumer smart meters, cyber vulnerabilities in AMI can risk the power system's confidentiality, integrity, availability, and accountability. This study reviews India's national regulatory and policy framework for cyber security in the power sector. Based on the theory of security economics, contracts between discoms and AMI Service Providers (AMISP) in five states and stakeholder consultations, the study recommends four ways to make India's AMI rollout more resilient.
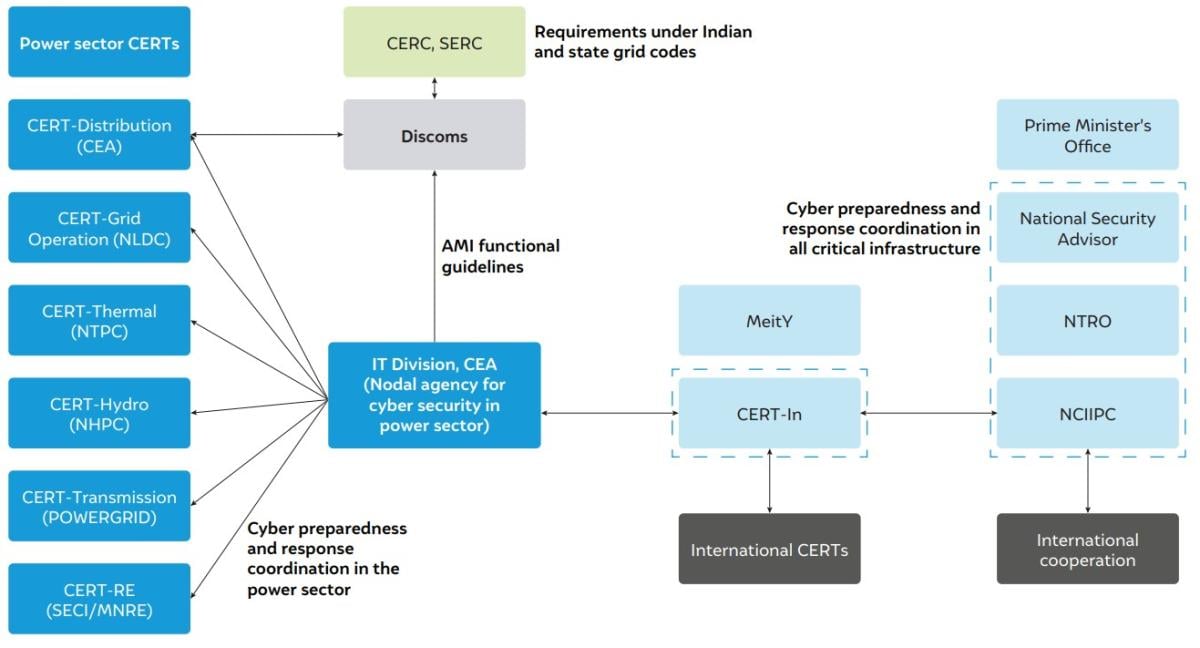
India has a robust policy framework for power sector cyber security
Source: Authors’ illustration
Smart electricity meters are the last-mile technology to help make the power grid become more flexible, and financially and technically efficient. With supporting infrastructure, smart meters can instantly communicate energy consumption, power demand on/off status, tamper information, etc. to utilities, facilitating real-time power supply and demand balancing, efficient billing, and network maintenance. To realise these benefits, there is an aggressive push by the Government of India and electricity distribution companies (discoms) to install 250 million smart meters by March 2025 (MoP 2021) in place of conventional meters. However, this advanced metering infrastructure (AMI) is an information and communication technology (ICT) network operating within a network of legacy electrical and electro-mechanical machines. Like any ICT, the smart meter network carries cyber vulnerabilities that can put the physical system’s confidentiality, integrity, availability, and accountability at risk (Cleveland 2008). This brief explains the risks and vulnerabilities that can hinder India’s smart meter and related infrastructure rollout and facilitate a deeper discourse on this critical issue.
The national critical infrastructure cyber security framework and guidelines are quite comprehensive. The Information Technology Act, 2000 contains specific provisions for the cyber protection of critical infrastructure. The Act set up the National Critical Information Infrastructure Protection Centre (NCIIPC) and the Indian Computer Emergency Response Team (CERT-In) to provide incident response and operational support to critical infrastructure operators. Six sectoral CERTs have been established for securing power infrastructure, with one of them dedicated to the distribution sector. Further, the standard bidding document (SBD) for advanced metering infrastructure service providers (AMISPs) notified by REC Limited specifies security-related compliances by relevant stakeholders. A detailed examination of actual contracts of 5 discoms with AMISPs and semi-structured interviews with 18 stakeholders from discoms, electricity regulators and planners, public sector undertakings, AMI vendors, and security consultants complements our review of the overall cyber security policy framework.
We find that discoms currently lack the technical capacity to act on the relevant CERT’s advisories. As AMI grows in size and complexity, the risks to the power system could amplify as discoms struggle to procure the tools and services to bolster their security posture due to financial constraints. The AMISP contracts contain varying compliance measures across discoms. For example, among the reviewed states, Haryana’s discoms have the most comprehensive requirements for the AMISP on data retention, system security, and disaster recovery. Rajasthan’s discoms have focused on the physical integrity of the system, but measures on system availability and AMISP’s accountability can be improved. Discoms in Assam impose higher maximum penalties on AMISP for non-compliance with contract provisions than the other states. Furthermore, the role of discoms in AMI operation is mainly supervisory. Contractual obligations on the AMISP for training discom staff may be inadequate to equip them for situational awareness of the system, leading to principal-agent problems. The frequency of event reporting and security audits, meant to provide discoms with detailed information on the system’s preparedness to deal with cyber threats, varies from monthly in Jammu & Kashmir to quarterly in Haryana to annually in Maharashtra.
Based on our analysis, the theory of security economics in networked systems, and international practices in securing AMI, we make four key recommendations:
1) Harmonise critical provisions to a common baseline in all discom–AMISP contracts. The SBD issued by REC partly resolves the issue of lack of uniform contractual obligations by providing a baseline for all contracts signed from September 2022 onwards. However, the Forum of Regulators (FoR) must work with state electricity regulators to harmonise critical contractual obligations across contracts, such as audit requirements and non-compliance penalties.
2) Resolve the information asymmetry between discoms and AMISPs. AMISPs may have greater visibility on system security than discoms, which would restrict discoms from fulfilling their regulatory and legal obligations. A deeper technical capacity to vet and act on audit reports and dedicated teams to monitor system operations and security within discoms can help resolve information asymmetries. Further, vendors/solution providers must be held responsible for disclosing vulnerabilities in the supplied hardware and software solutions. They must also be mandated to ensure the availability of necessary update patches and mitigating controls in a time-bound manner.
3) Provide deeper technical support to discoms and develop a local ecosystem for security services. Central government agencies such as the Central Electricity Authority and CERT-In must actively collaborate with other stakeholders in the system, such as public sector undertakings and the private sector, to create a security ecosystem. Discoms can be supported by creating a pool of qualified vendors to provide AMI-specific services, developing tools and metrics to help them assess and improve their security preparedness, real-time analytical support, and physical infrastructure such as equipment testing facilities.
4) Strengthen the provisions to hold discoms and vendors accountable for lapses in cyber security. Efficient disclosure of relevant information helps improve accountability and therefore build resilience to future threats. Information disclosure obligations at all levels and penalties for non-disclosure play a critical role in improving the cyber security posture of ICT systems. Regulations must incorporate incentives and mandates to ensure that discoms and vendors of critical AMI components adhere to the highest standards of security and disclosure practices.
Cyber security not only requires guarding against known threats but also preparing for unknown threats. It is as much about technology as about people, processes and governance. Given that AMI is likely to witness a rapid expansion in the next few years, all key stakeholders across the various levels of government, the discoms, the regulators, and the private sector have to act in a collaborative manner to build a resilient and smart power system.

How can India Scale Up Electricity Demand-side Management?

Improving Discoms’ Financial Viability

Assessing the Value of Offshore Wind for India’s Power System in 2030

Enabling a Consumer-centric Smart Metering Transition in India